Snipe-IT: CVE-2025-63601 - Post-Authenticated Remote Command Execution via Backup Restore Feature
I identified a Remote code execution vulnerability (CVE-2025-63601) in Snipe-IT’s backup restore feature, rooted in unsafe file extraction logic.
Summary
Product: Snipe-IT
Severity: Critical
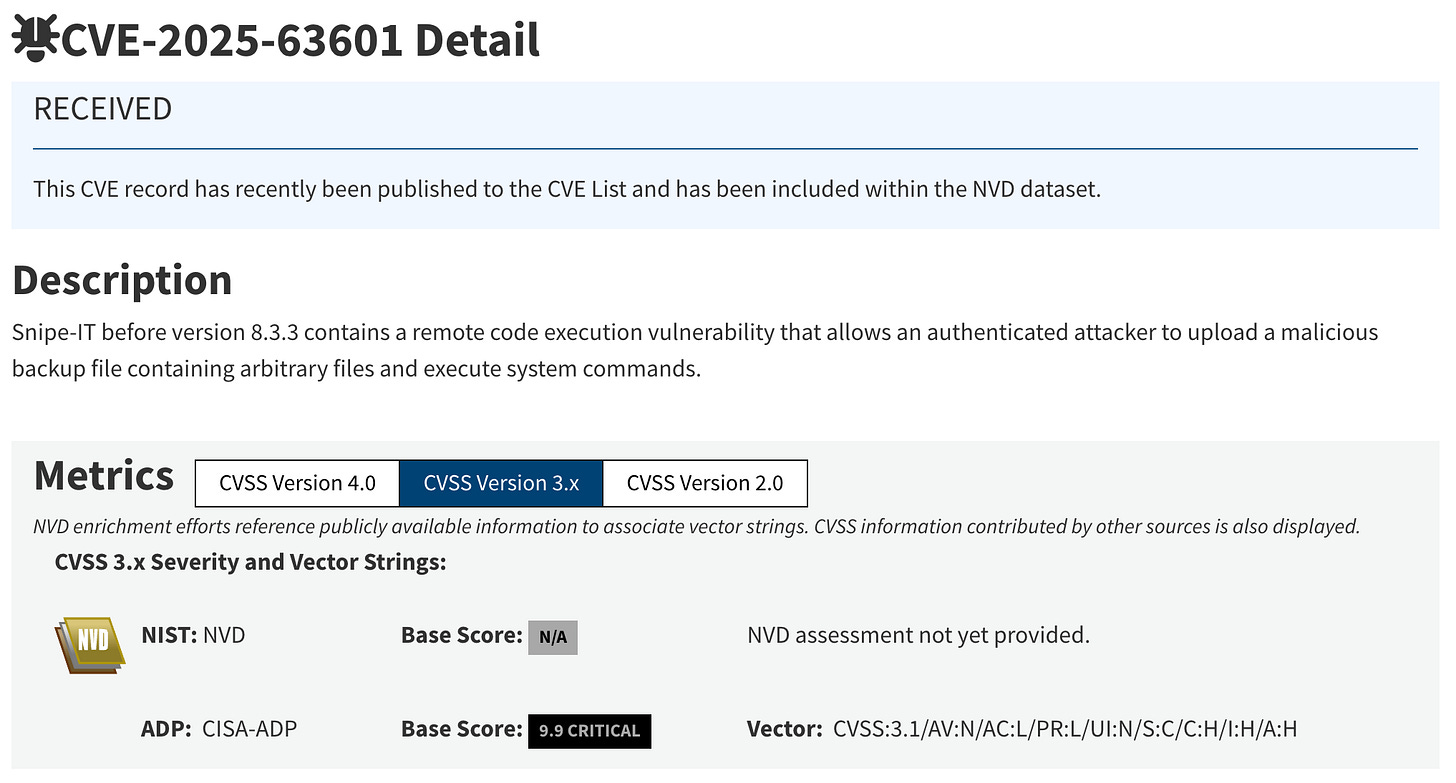
Affected Version(s): ≤ 8.3.3
Fixed Version(s): 8.3.3 or later
CVE Number: CVE-2025-63601
Timeline
2025.09.26: Sent report to security@snipeitapp.com
2025.10.07: Snipe-IT team Release of version 8.3.3 containing the patch
2025.10.30: CVE-2025-63601 RESERVED
2025.11.05: Public release
Description
Presentation
Snipe-IT is an open source asset management system based on the PHP framework Laravel.
Root Cause Analysis
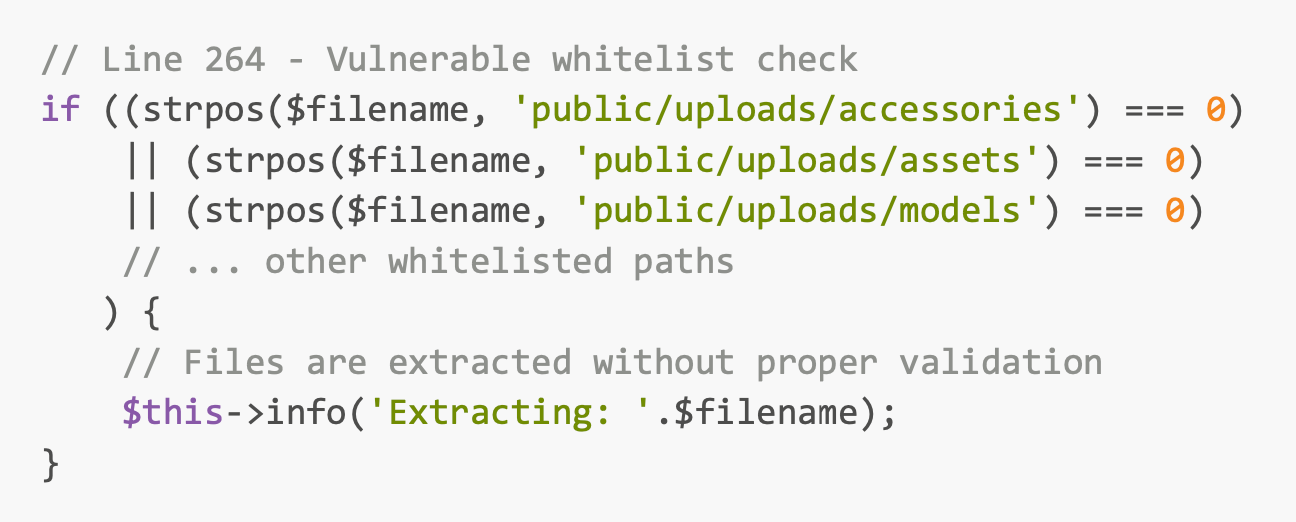
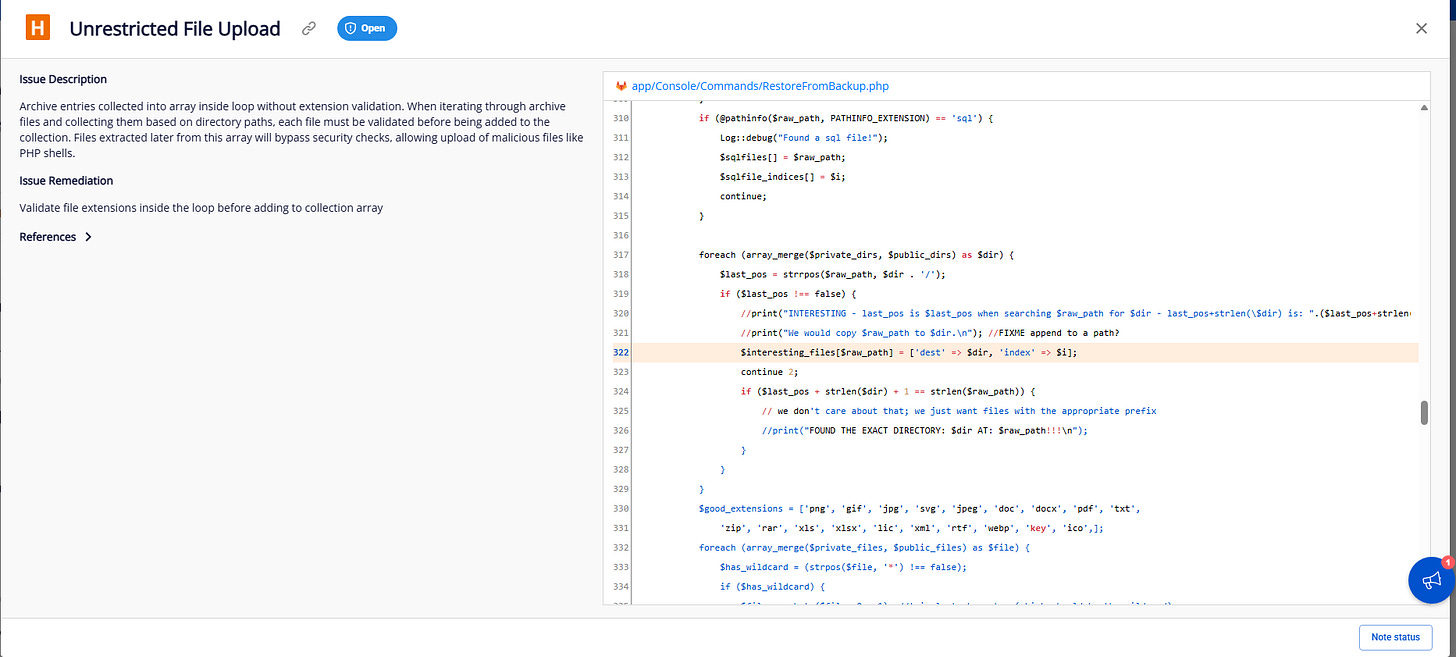
File: app/Console/Commands/RestoreFromBackup.php
Insufficient Path Validation
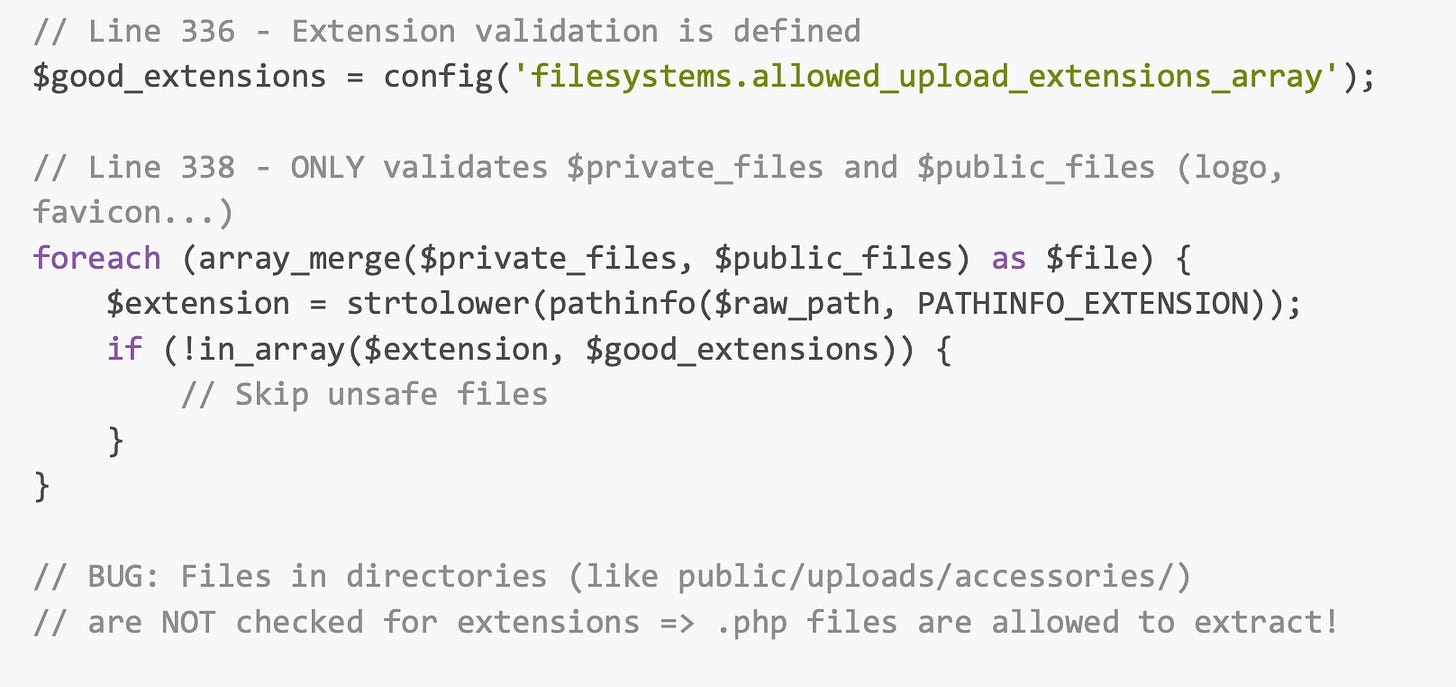
Missing File Type Validation
Extension validation only applies to specific files, NOT to directory contents!
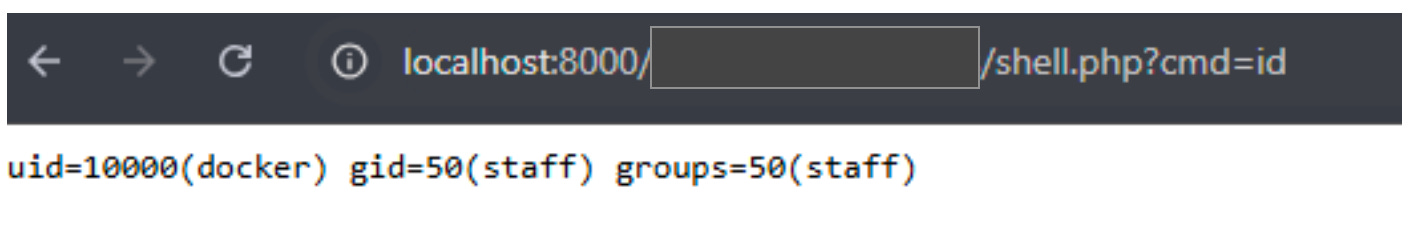
Result: An Authenticated user (Admin) can put a malicious php file successfully via Backup Restore feature.
References
https://www.cve.org/CVERecord?id=CVE-2025-63601
https://nvd.nist.gov/vuln/detail/CVE-2025-63601
https://github.com/grokability/snipe-it/releases/tag/v8.3.3
How FPT AppSec Code Scan trace CVE-2025-63601
During our analysis of CVE-2025-63601, we relied on ASPM’s code scan engine — its static analysis rules (taint tracing, data-flow tracking,…) combined with AI-assisted pattern recognition made it easy to pinpoint the vulnerable code path.
Learn more about FPT AppSec and try it here https://fptcloud.com/product/fpt-appsec-nen-tang-tu-dong-hoa-bao-mat/